
- 이전에 작성한 ec2 파일을 옮긴다.

- 이제 vpc 파일에 생성된 vpc를 가져와야 한다.

- vpc 파일에서 가져온다.

- 아래와 같이 변경된다.
코드 보여준다.
- VPC.tf 코드
provider "aws" {
region = "ap-northeast-2"
}
resource "aws_vpc" "vpc-10-10-0-0" {
cidr_block = "10.10.0.0/16"
instance_tenancy = "default"
enable_dns_hostnames = true
tags = {
Name = "vpc-10-10-0-0"
}
}
resource "aws_subnet" "sub-pub1-10-10-1-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
cidr_block = "10.10.1.0/24"
availability_zone = "ap-northeast-2a"
map_public_ip_on_launch = true
tags = {
Name = "sub-pub1-10-10-1-0"
}
}
resource "aws_subnet" "sub-pub2-10-10-2-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
cidr_block = "10.10.2.0/24"
availability_zone = "ap-northeast-2c"
map_public_ip_on_launch = true
# 이 부분 때문에 public ip가 부여 된다.
tags = {
Name = "sub-pub1-10-10-2-0"
}
}
resource "aws_subnet" "sub-pri1-10-10-3-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
cidr_block = "10.10.3.0/24"
availability_zone = "ap-northeast-2a"
# pri이기 떄문에 pub과 다르게 이부분이 없다.
tags = {
Name = "sub-pub1-10-10-3-0"
}
}
resource "aws_subnet" "sub-pri2-10-10-4-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
cidr_block = "10.10.4.0/24"
availability_zone = "ap-northeast-2c"
tags = {
Name = "sub-pub1-10-10-4-0"
}
}
# internet gateway
resource "aws_internet_gateway" "igw-vpc-10-10-0-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
tags = {
Name = "igw-vpc-10-10-0-0"
}
}
#routing table 생성
resource "aws_route_table" "rt-pub-vpc-10-10-0-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.igw-vpc-10-10-0-0.id
}
tags = {
Name = "rt-pub-vpc-10-10-0-0"
}
}
# pub 라우팅 테이블에 associate 하기
resource "aws_route_table_association" "rt-pub-as1-vpc-10-10-0-0" {
subnet_id = aws_subnet.sub-pub1-10-10-1-0.id
route_table_id = aws_route_table.rt-pub-vpc-10-10-0-0.id
}
resource "aws_route_table_association" "rt-pub-as2-vpc-10-10-0-0" {
subnet_id = aws_subnet.sub-pub2-10-10-2-0.id
route_table_id = aws_route_table.rt-pub-vpc-10-10-0-0.id
}
resource "aws_route_table" "rt-pri1-vpc-10-10-0-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_nat_gateway.natgw-2a.id
}
tags = {
Name = "rt-pri1-vpc-10-10-0-0"
}
}
resource "aws_route_table" "rt-pri2-vpc-10-10-0-0" {
vpc_id = aws_vpc.vpc-10-10-0-0.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_nat_gateway.natgw-2c.id
}
tags = {
Name = "rt-pri2-vpc-10-10-0-0"
}
}
resource "aws_route_table_association" "rt-pri1-as1-vpc-10-10-0-0" {
subnet_id = aws_subnet.sub-pri1-10-10-3-0.id
route_table_id = aws_route_table.rt-pri1-vpc-10-10-0-0.id
}
resource "aws_route_table_association" "rt-pri2-as2-vpc-10-10-0-0" {
subnet_id = aws_subnet.sub-pri2-10-10-4-0.id
route_table_id = aws_route_table.rt-pri2-vpc-10-10-0-0.id
}
# EIP 받아오기
resource "aws_eip" "nat-2a" {
vpc = true
}
resource "aws_eip" "nat-2c" {
vpc = true
}
resource "aws_nat_gateway" "natgw-2a" {
allocation_id = aws_eip.nat-2a.id
subnet_id = aws_subnet.sub-pub1-10-10-1-0.id
tags = {
Name = "gw NAT-2a"
}
}
resource "aws_nat_gateway" "natgw-2c" {
allocation_id = aws_eip.nat-2c.id
subnet_id = aws_subnet.sub-pub2-10-10-2-0.id
tags = {
Name = "gw NAT-2c"
}
}
- 같은 폴더의 ec2.tf 코드
data "aws_ami" "amzn2" {
most_recent = true
filter {
name = "name"
values = ["amzn2-ami-hvm-2.0.????????.?-x86_64-gp2"]
}
filter {
name = "virtualization-type"
values = ["hvm"]
}
owners = ["amazon"] # Canonical
}
resource "aws_security_group" "allow_web-sg" {
name = "allow_web-sg"
description = "Allow web-sg inbound traffic"
vpc_id = aws_vpc.vpc-10-10-0-0.id
ingress {
description = "web from VPC"
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
tags = {
Name = "allow_web"
}
}
resource "aws_instance" "bastion" {
ami = data.aws_ami.amzn2.id
instance_type = "t2.micro"
key_name = "AWS_ISBAEK"
vpc_security_group_ids = [aws_security_group.allow_web-sg.id]
availability_zone = "ap-northeast-2a"
subnet_id = aws_subnet.sub-pub1-10-10-1-0.id
user_data = file("./userdata.sh")
root_block_device {
volume_size = 30
}
tags = {
Name = "bastion"
}
}
resource "aws_instance" "web-2a" {
ami = data.aws_ami.amzn2.id
instance_type = "t2.micro"
key_name = "AWS_ISBAEK"
vpc_security_group_ids = [aws_security_group.allow_web-sg.id]
availability_zone = "ap-northeast-2a"
subnet_id = aws_subnet.sub-pri1-10-10-3-0.id
user_data = file("./userdata.sh")
root_block_device {
volume_size = 30
}
tags = {
Name = "web-2a"
}
}
resource "aws_instance" "web-2c" {
ami = data.aws_ami.amzn2.id
instance_type = "t2.micro"
key_name = "AWS_ISBAEK"
vpc_security_group_ids = [aws_security_group.allow_web-sg.id]
availability_zone = "ap-northeast-2c"
subnet_id = aws_subnet.sub-pri2-10-10-4-0.id
user_data = file("./userdata.sh")
root_block_device {
volume_size = 30
}
tags = {
Name = "web-2c"
}
}



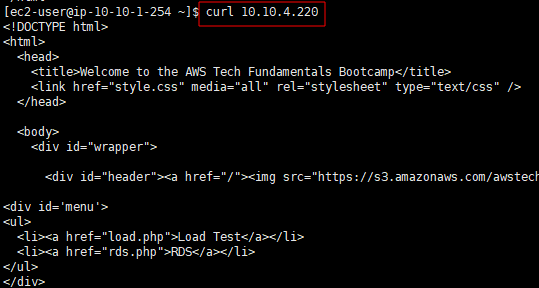
- 이전에 작성한 스크립트 파일이 제대로 private subnet에 생성된 web에 적용된 것을 볼 수 있다.
- 즉, nat gateway가 제대로 적용된 것을 알 수 있다.
728x90
'Cloud > Terraform' 카테고리의 다른 글
| Terraform - Amazon Machin Image(AMI) 생성 (0) | 2022.07.09 |
|---|---|
| Terraform - Private Subnet에 Application Load Balancer 구성 (0) | 2022.07.09 |
| Terraform - Elastic IP 생성 및 NAT Gateway 구성 (0) | 2022.07.09 |
| Terraform - Private subnet용 Route table 구성 (0) | 2022.07.09 |
| Terraform - Internet Gateway 생성 및 Public subnet용 Route table 구성 (0) | 2022.07.09 |