- 인터넷 게이트웨이 생성
# 05.ig.tf
resource "aws_internet_gateway" "tf-ig" {
vpc_id = aws_vpc.tf-vpc.id
tags = {
Name = "tf-ig"
}
}- 인터넷 게이트웨이 생성
- Routing Table 생성 및 IG 연결
# 06.rt.tf
resource "aws_route_table" "tf-rt-pub" {
vpc_id = aws_vpc.tf-vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.tf-ig.id
}
tags = {
Name = "tf-rt-pub"
}
}- routing table 생성 및 IG 연결
- Routing Table에 Subnet 연결
# 07.rt-sb-as.tf
resource "aws_route_table_association" "tf-pub-a" {
subnet_id = aws_subnet.tf-pub-a.id
route_table_id = aws_route_table.tf-rt-pub.id
}
resource "aws_route_table_association" "tf-pub-c" {
subnet_id = aws_subnet.tf-pub-c.id
route_table_id = aws_route_table.tf-rt-pub.id
}- routing table에 subnet 연결
- NAT-Gateway 생성 및 EIP 적용
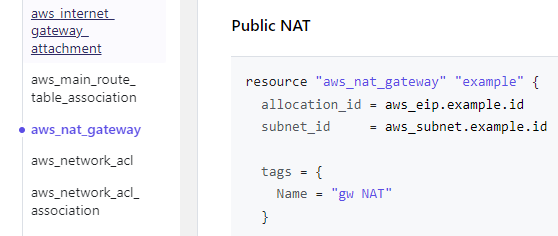

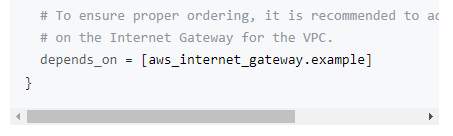
- Terraform은 순서에 상관없이 작업이 되지만 가끔씩 위와 같이 먼저 선어되어야 실행이 되는 구문들이 있다.
# 08.ng-eip.tf
resource "aws_eip" "tf-ngwip" {
vpc = true
}
resource "aws_nat_gateway" "tf-ng" {
allocation_id = aws_eip.tf-ngwip.id
subnet_id = aws_subnet.tf-pub-a.id
tags = {
Name = "tf-ng"
}
}- nat-gateway 생성 및 nat-gateway는 eip가 필요하기 때문에 eip 생성과 동시에 nat-gateway에 집어넣는다.
- NAT-Gateway를 위한 Routing-table 생성 및 적용
# 09.ng-rt.tf
resource "aws_route_table" "tf-rt-pri" {
vpc_id = aws_vpc.tf-vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_nat_gateway.tf-ng.id
}
tags = {
Name = "tf-rt-pri"
}
}- nat-gateway를 적용할 routing-table 생성 및 nat-gateway 적용
- NAT-Gateway 서브넷 포함 시키기
# 10.ng-sb-as.tf
resource "aws_route_table_association" "tf-web-a" {
subnet_id = aws_subnet.tf-web-a.id
route_table_id = aws_route_table.tf-rt-pri.id
}
resource "aws_route_table_association" "tf-web-c" {
subnet_id = aws_subnet.tf-web-c.id
route_table_id = aws_route_table.tf-rt-pri.id
}
resource "aws_route_table_association" "tf-was-a" {
subnet_id = aws_subnet.tf-was-a.id
route_table_id = aws_route_table.tf-rt-pri.id
}
resource "aws_route_table_association" "tf-was-c" {
subnet_id = aws_subnet.tf-was-c.id
route_table_id = aws_route_table.tf-rt-pri.id
}
resource "aws_route_table_association" "tf-rds-a" {
subnet_id = aws_subnet.tf-rds-a.id
route_table_id = aws_route_table.tf-rt-pri.id
}
resource "aws_route_table_association" "tf-rds-c" {
subnet_id = aws_subnet.tf-rds-c.id
route_table_id = aws_route_table.tf-rt-pri.id
}- Security-Group 생성하기
# 11.sg.tf
resource "aws_security_group" "tf-sg" {
name = "tf-sg"
description = "Allow inbound traffic"
vpc_id = aws_vpc.tf-vpc.id
ingress = [
{
description = "SSH"
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
prefix_list_ids = null
security_groups = null
self = null
},
{
description = "HTTP"
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
prefix_list_ids = null
security_groups = null
self = null
},
{
description = "ICMP"
from_port = -1
to_port = -1
protocol = "icmp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
prefix_list_ids = null
security_groups = null
self = null
},
{
description = "MYSQL"
from_port = 3306
to_port = 3306
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
prefix_list_ids = null
security_groups = null
self = null
},
{
description = "FTP"
from_port = 60000
to_port = 60100
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
prefix_list_ids = null
security_groups = null
self = null
},
{
description = "FTP"
from_port = 21
to_port = 21
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
prefix_list_ids = null
security_groups = null
self = null
}
]
egress {
description = "all"
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
ipv6_cidr_blocks = ["::/0"]
}
tags = {
Name = "tf-sg"
}
}- sh 파일 작성
# install.sh
#! /bin/bash
sudo su -
yum install -y httpd
cat > /var/www/html/index.html << EOF
<html>
<body>
<h1>AWS_TERRAFORM_WEBSERVER</h1>
</body>
</html>
EOF
systemctl start httpd
- EC2 Instance 생성
# 12.ec.tf
data "aws_ami" "amzn" {
most_recent = true
filter {
name = "name"
values = ["amzn2-ami-hvm-*-x86_64-gp2"]
}
filter {
name = "virtualization-type"
values = ["hvm"]
}
owners = ["amazon"]
}
resource "aws_instance" "tf-bastion" {
ami = data.aws_ami.amzn.id
instance_type = "t2.micro"
key_name = "tf-key"
vpc_security_group_ids = [aws_security_group.tf-sg.id]
availability_zone = "ap-northeast-2a"
subnet_id = aws_subnet.tf-pub-a.id
associate_public_ip_address = true
user_data = file("./install.sh")
tags = {
Name = "tf-bastion"
}
}
output "public-ip" {
value = aws_instance.tf-bastion.public_ip
}728x90
'Cloud > Terraform' 카테고리의 다른 글
| Terraform - 07/20 (0) | 2022.07.20 |
|---|---|
| Terraform - 07/19 (0) | 2022.07.19 |
| Terraform - 07/14 (0) | 2022.07.14 |
| Terraform - RDS 생성 (0) | 2022.07.14 |
| Terraform - Auto Scaling Tracking Policy 생성 및 Load Test로 Auto Scaling 테스트 (0) | 2022.07.10 |